What Is a USB Drop Attack and How Can You Prevent It? - MUO - MakeUseOf
If you ever find a Universal Serial Bus (USB) drive in your driveway, a parking lot, or other commonplaces, never plug it into your PC. The cute-looking USB stick might have malicious software or code to carry out a USB drop attack.
What Is a USB Drop Attack?
In a USB drop attack, a cybercriminal strategically places an infected USB in the proximity of a victim so that the target can find it and plug it into a computer out of curiosity.
USB drop attacks are social engineering attacks that rely on how humans think and act in different situations.
When a person finds a USB stick, either they want to return it to the real owner or keep it. In both cases, they will likely plug the USB stick into a device to find out what it contains. And once the USB drive is plugged in, troubles start.
4 Types of USB Attacks
Let's first go over the main types of USB attacks you should be aware of.
1. Social Engineering
USB sticks have files with inviting names like "Top Secret". And these files have links to malicious sites. Clicking on them takes victims to phishing sites that can dupe victims into sharing confidential information, giving money, or installing malware on their computers.
2. Malicious Code
This is one of the most common types of USB drop attacks. USB sticks have files that release malicious code when somebody clicks on them, installing malware automatically on the victim's system. Then, attackers can steal confidential data or, in the case of ransomware, encrypt files.
3. Human Interface Device Spoofing
In a Human Interface Device (HID) spoofing attack, a connected USB drive misdirects a computer to think that a keyboard is attached. Then, the USB drive injects pre-configured keystrokes that give hackers remote computer access.
Once the remote connection is established, hackers can steal confidential information or install various types of malware on the victim's computer.
4. USBKill
USBKill attacks, though not common, are designed to destroy computers. In such an attack, a USBKill stick that looks precisely the same as any other USB thumb drive stores power using a capacitor. It then releases a high-voltage back through data pins of that same USB connection. This destroys the computer as USB data pins are designed to handle a tiny amount of power—just enough to send signals.
Why Cybercriminals Attempt USB Drop Attacks
Why would hackers even bother with USB drop attacks? There are a few key reasons. Using such an attack, cybercriminals can:
- Steal logins and passwords;
- Install ransomware to encrypt data or exfiltrate data;
- Take over victims' computers remotely to spy on them by using their webcams and microphones;
- Destroy victims' computers.
But the main objective of USB drop attacks is money.
Once hackers get hold of your sensitive data or device, they can ask for a ransom after encrypting your data or sell your confidential information on the dark web to make cash.
How to Prevent a USB Drop Attack
You might often need to open a USB drive, without knowing if the USB drive is free from viruses or malware. For example, your friend or relative has asked you to print a few documents from a USB stick. You would just trust that everything is fine, right? They might not even be aware that the USB is compromised.
What's more, sometimes, there are situations when you have to know what's on an unfamiliar USB stick.
Let's consider some efficient ways to help you avoid falling victim of a USB drop attack.
Only Use Trusted USB Drives
The best way to avoid a USB attack is to only plug trusted USB devices into your computer. If you're not sure whether a USB drive is clean or not, avoid plugging it into your computer system.
Install a Reliable Security Program
Installing and regularly updating a comprehensive antivirus program can protect your computer system from many known threats. Make sure your PC has the latest security software installed.
If the nature of your work requires you to open unknown USB drives frequently, you should look for a security solution that has capabilities beyond virus and malware mitigation.
The security solution you pick must have a feature that will not authorize any HIDs unless you input a code with an already authorized HID. This feature will protect your computer system from HID spoofing.
Disable AutoPlay on Your PC
The AutoPlay feature is a helpful feature in Windows. It allows Windows Explorer to automatically perform different actions depending on the media type on the connected device.
But with AutoPlay enabled, malicious code or malware can be automatically executed when you connect an infected USB drive to your computer system.
So, disabling the AutoPlay feature can help you avoid getting infected while inserting unknown USB drives into your Windows PC.
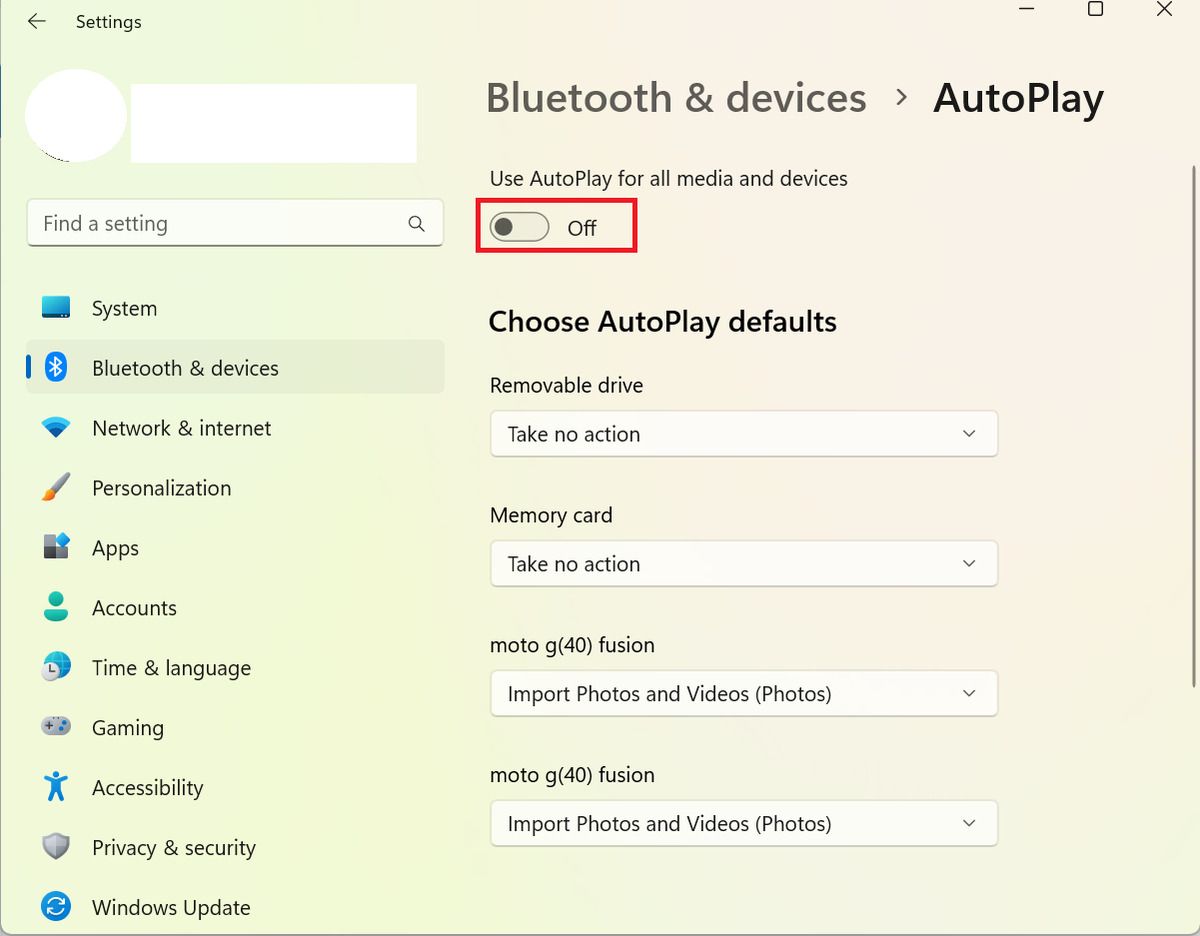
Here is the simple process to disable AutoPlay on a Windows PC:
- Go to Settings > Bluetooth and devices.
- Scroll down in the right sidebar, and click on the AutoPlay tab.
- Toggle off the Use AutoPlay for all media and devices option.
Use Virtualization Software to Open USB Drives
Though this is not a foolproof method, opening an unknown USB drive in a virtual environment to find out what it contains can offer you reasonable protection.
You can use Oracle's free VirtualBox program to create a virtual environment on your computer. Make sure you disable file sharing between the host computer and the virtual machine before connecting an unfamiliar USB device to a virtual machine on your computer.
Use an Air-Gapped Computer
If you need to know what a USB drive contains, use an air-gapped computer. An air-gapped computer means the PC is not connected to any computer network or the internet. And you should use this air-gapped computer only for opening unknown USB drives.
Don't Fall for a Dropped USB Drive
Carrying out USB drop attacks is easy for hackers as buying USB flash drives is inexpensive. The best way to protect from a USB drop attack or any other type of attack involving a USB drive is simply to never trust an unknown USB drive.
If you must open an unknown USB drive, using an air-gapped PC or a virtual environment can offer reasonable protection. If other family members use your PC, disabling USB ports can be a good strategy to stay protected.
Comments
Post a Comment